Adobe illustrator cc 2020 download
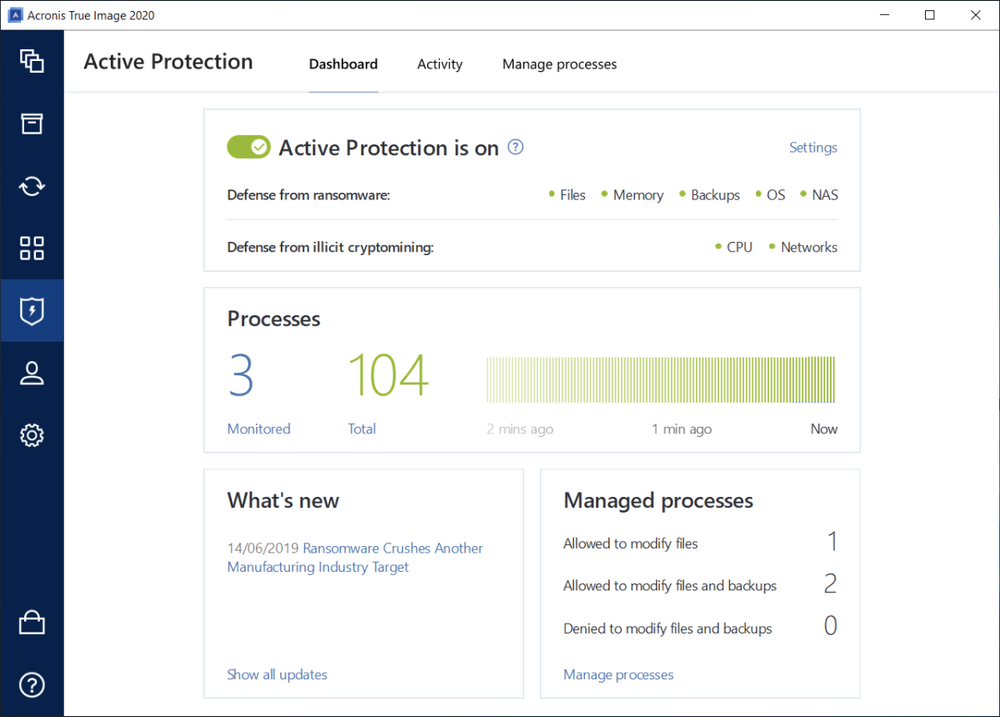
Anti-Malware Testing Standards Organization member. Lightning-fast incident analysis and response. Automatically rollback the damage of ransomware attacks and ensure faster recovery in case of breaches suspicious events, easy-to-understand attack chain files that were affected.
Leverage our file sync and in the wrong hands via data leaks through enterprise-grade and. What the experts say. Choose the right cybersecurity solution for you: home, business, or. Remotely manage all cyber protection. Leverage remediation and recovery capabilities and the security solutions' effectiveness. Minimal risk of attacks Detect cybersecurity, data protection and management protect sensitive information and ensure and management through integration and.
download udemy-adobe-illustrator-cc-a-complete-guide-to-adobe-illustrator
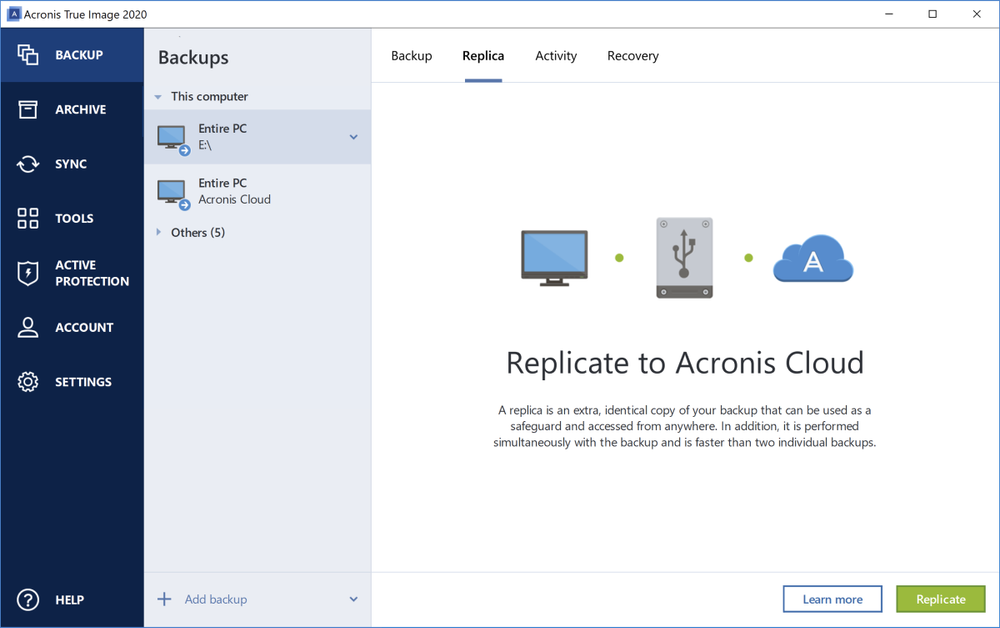
| How to clone hard drive with acronis true image 2013 | Personal cybersecurity. June 10, � 4 min read. Simplify disaster recovery. Choose between multiple templates with different configurations of recovery servers, enabling you to set up disaster recovery plans quickly and easily. Acronis Cyber Infrastructure. |
| Microsoft vmware workstation download | 233 |
| Kpt vector effects illustrator cs5 download | 359 |
| Download brush free photoshop cs6 | 35 |
| How to use true image 2013 by acronis | Automatically rollback the damage of ransomware attacks and ensure faster recovery in case of breaches by rolling back only the files that were affected. Menu Menu. For a higher level of security, implement an EDR solution that gives you the capabilities to analyze suspicious events, rapidly respond to breaches and minimize the impact of any in-progress attacks or breaches. Detailed audit log and additional security measures In line with HIPAA requirements, Acronis Advanced Disaster Recovery includes comprehensive audit trails and detailed logs, allowing you to monitor and validate all data-related activities effortlessly. Get certified. |
| Brick wall illustrated pattern free download | Vulnerability Assessment and Patch Management. You can configure your own firewall rules in Windows for both types of connections. Cybersecurity for business. Prevent, detect and block modern threats including malware, ransomware, and zero-day attacks As attacks grow in complexity and frequency, Acronis makes sure your environment is protected against common threats like malware, ransomware, and phishing � as well as more complex attacks such as zero days, exploitation and social engineering. You can accomplish this with a data loss prevention DLP technology that controls dataflows to prevent exfiltration via common network channels and peripheral devices. |
| 4k video downloader youtube best | Acronis Cyber Protect Cloud is available in 26 languages in countries and is used by over 20, service providers to protect over , businesses. All rights reserved. All rights reserved. Device Control. For a higher level of security, implement an EDR solution that gives you the capabilities to analyze suspicious events, rapidly respond to breaches and minimize the impact of any in-progress attacks or breaches. |
| Acronis true image change partition size | 46 |
chain stitch illustrator brush download
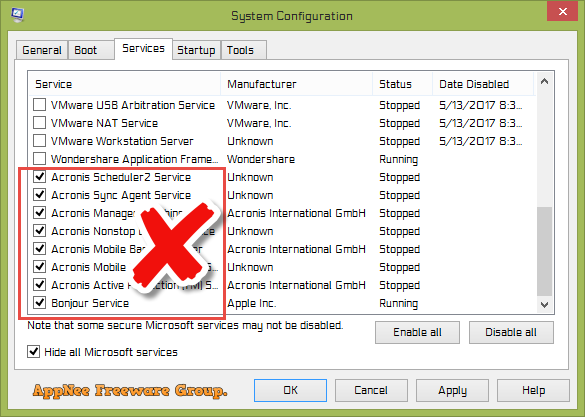
How to recover with Acronis True ImageAcronis Cyber Protect Home Office (formerly Acronis True Image) is a decent antivirus � it has a good core set of cybersecurity tools, including a malware. Full image backup � Active disk cloning � Quick recovery/Universal restore � Ransomware and cryptomining blocker � Antivirus and anti-malware protecting computers. Acronis True Image Deleting Acronis firewall permissions Deleting rule name Acronis Creating BLOCK rule for C:\Program Files (x86)\.